Containing the Danger: A High-Level Overview of Browser Isolation in ZIA
Beyond Signatures: Containing the Danger
A High-Level Overview of Browser Isolation in ZIA
In today's ever-evolving threat landscape, traditional signature-based security measures are like building a fortress wall—strong, but ultimately useless against an attacker who can simply tunnel underneath. Attackers constantly develop new methods to bypass defenses, making it crucial for organizations to adopt more advanced, proactive security solutions. One such solution gaining significant traction is browser isolation, and Zscaler Internet Access (ZIA) offers a robust implementation to neutralize threats before they can even reach your network.
The Problem with Trusting the Web
For years, cybersecurity relied on identifying known malicious code or patterns (signatures) and blocking them. This approach is fundamentally reactive. It struggles with:
- Zero-Day Exploits: New, unknown vulnerabilities that don't have a signature yet.
- Polymorphic Malware: Malicious code that constantly changes to evade signature-based detection.
- Sophisticated Phishing: Credential theft sites that look legitimate and may not be flagged immediately.
Every time a user browses a website, they are essentially inviting code from an untrusted source to run on their machine. Browser isolation changes this paradigm entirely by assuming no website is safe.
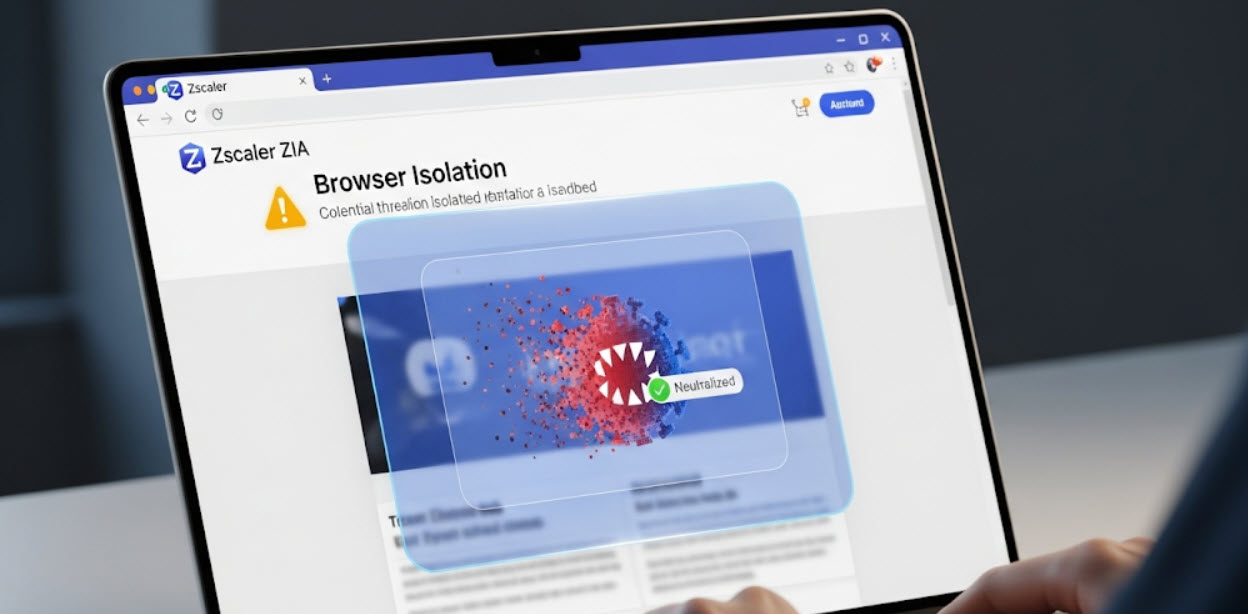
How ZIA's Browser Isolation Works
1. User's Device
User clicks a link to an unknown or risky website.
2. Zscaler Cloud
The website is rendered in a secure, disposable container far from your network.
3. Safe Content Stream
Only safe, interactive pixels are streamed to the user's browser. No active code ever reaches the endpoint.
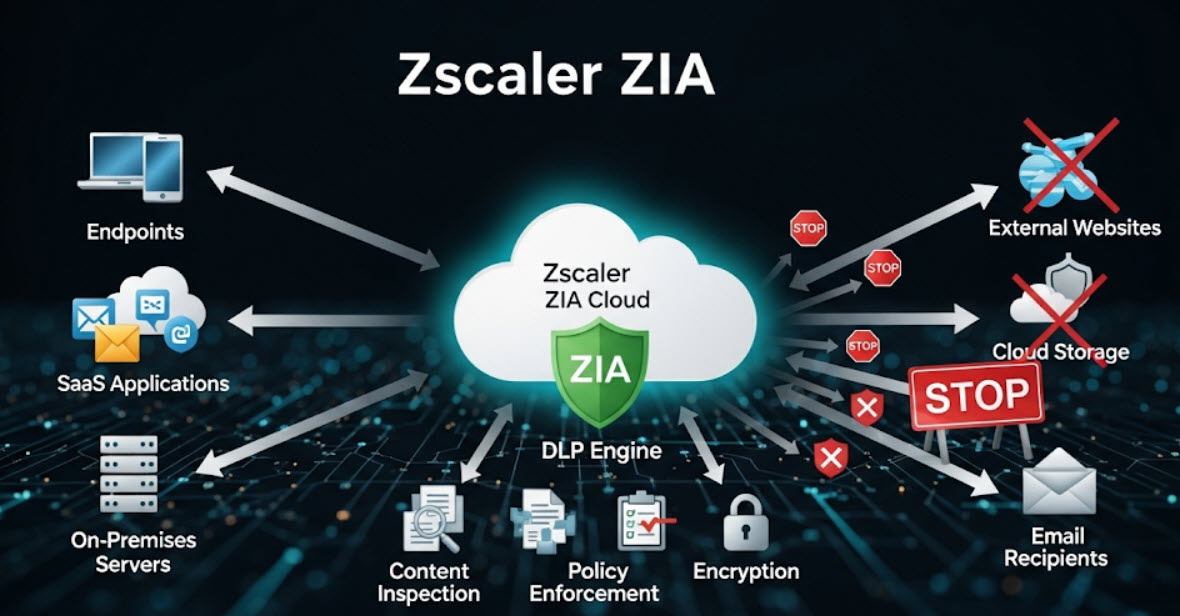
The "Airlock" for Your Web Traffic
Think of it as a digital airlock. The Zscaler cloud acts as a neutral territory. It opens the potentially dangerous package (the website) inside a sealed, disposable room. It then shows you a video feed of what's inside. You can interact with the contents, but nothing tangible—no active code, no malware, no threats—can cross the barrier to your device.
This approach provides comprehensive protection by design:
- Complete Threat Isolation: Since no web code runs on the user's device, all browser-based exploits are rendered harmless. Ransomware, phishing kits, and other malware are completely contained.
- Data Leakage Prevention: Policies can be set to prevent users from uploading sensitive data to personal cloud storage or copy/pasting information into unauthorized web forms.
- Seamless User Experience: To the user, the experience is nearly identical to native browsing. The pixel stream is fast and interactive, preserving the functionality of the website without the risk.
Conclusion: A Zero Trust Approach to Browsing
Browser isolation is a cornerstone of a modern Zero Trust architecture. By refusing to inherently trust any website, Zscaler ZIA eliminates an entire category of attack vectors. It moves security from a reactive game of "detect and respond" to a proactive state of "contain and neutralize." This containment strategy ensures that even the most sophisticated, unknown threats are stopped dead in their tracks, keeping your users and your organization secure.