Stopping Data Leaks: A High-Level Overview of Zscaler ZIA's DLP
Stopping Data Leaks: A High-Level Overview of Zscaler ZIA's DLP
A Guide to Data Loss Prevention with Zscaler ZIA
In today's digital-first world, data is the lifeblood of every organization. Protecting this data—from financial records and intellectual property to customer information—is not just an IT task; it's a critical business imperative. Data Loss Prevention (DLP) is the practice and set of tools used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. Zscaler Internet Access (ZIA) provides a powerful, cloud-native approach to DLP, helping organizations enforce their data protection policies consistently, no matter where their users are.
Why Cloud-Based DLP is Essential
Traditionally, DLP solutions were appliance-based, sitting within the corporate data center. This model is no longer effective. With the rise of remote work, cloud applications (SaaS), and personal devices (BYOD), users and data are everywhere. A modern security solution needs to follow the user and the data.
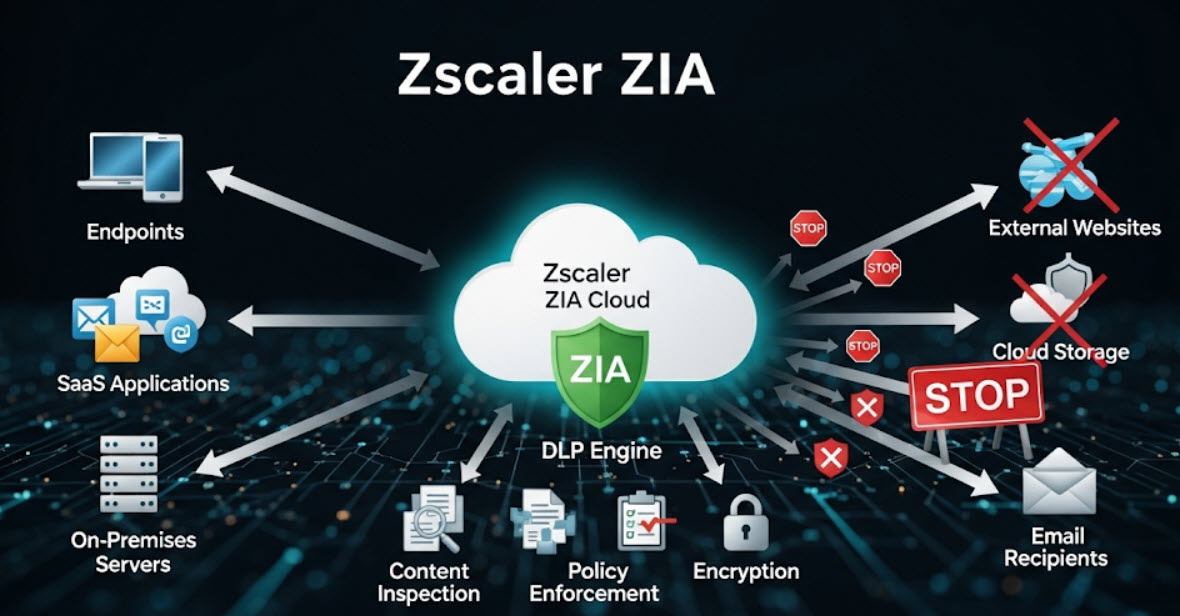
Zscaler's cloud-native architecture is perfectly suited for this new reality. By inspecting all internet-bound traffic in the cloud before it reaches its destination, ZIA can apply consistent DLP policies for every user, on any device, from any location. This eliminates the blind spots and policy gaps inherent in legacy security models.
Zscaler DLP Inspection Flow
User Traffic
From any device, any location
Zscaler Cloud
SSL Inspection & Policy Enforcement
Action Taken
Allow, Block, or Quarantine
Core Components of Zscaler DLP
Zscaler's DLP functionality is built on two primary components: DLP Engines and DLP Policies. Together, they provide a flexible and powerful framework for identifying and protecting sensitive data.
1. DLP Engines: Identifying the Data
DLP engines are the "what" of data protection—they define the sensitive information you want to protect. Zscaler offers a wide range of predefined engines and allows for the creation of custom ones.
- Predefined Engines: Zscaler provides hundreds of out-of-the-box dictionaries for common data types, such as credit card numbers (PCI), Social Security Numbers (PII), and health information (HIPAA). These are regularly updated to keep up with changing regulations.
- Custom Engines: For organization-specific data, you can build custom engines. This is often done using keywords (e.g., "Project Phoenix," "Confidential Internal Use Only") or Regular Expressions (Regex) to match specific data patterns unique to your business.
- Indexed Document Matching (IDM): For protecting structured data from a database or highly sensitive documents, IDM creates a secure hash-based index of the data. It can then identify full or even partial matches in outbound traffic without storing the original data in the cloud.
2. DLP Policies: Enforcing the Rules
If engines are the "what," policies are the "how." A DLP policy ties a DLP engine to users, groups, locations, and actions. It specifies the conditions under which a data leak is detected and what should happen when it is.
For example, a policy could be configured as follows:
"If a user from the 'Finance' group attempts to upload a document containing more than 10 credit card numbers (using the PCI DLP Engine) to a 'Personal Cloud Storage' web category, block the transfer and notify the security team."
The flexibility of the policy engine allows for granular control, minimizing false positives and ensuring that security rules don't interfere with legitimate business activities.
Incident Management and Reporting
Detection is only half the battle. Zscaler provides rich logging and reporting capabilities, giving security teams full visibility into potential data leaks. When a DLP policy is triggered, an incident is created with detailed context, including the user, the data that triggered the policy, the destination, and snippets of the matched content. This information is crucial for investigation, remediation, and refining DLP policies over time.
Conclusion
In a world defined by distributed workforces and cloud applications, protecting sensitive data requires a modern, cloud-first approach. Zscaler ZIA's DLP capabilities provide organizations with the tools they need to prevent data leaks, enforce compliance, and secure their most valuable assets. By moving inspection to the cloud and offering powerful, flexible policy controls, Zscaler ensures that your data protection follows your users, wherever they go.