Beyond Signatures: How Zscaler ZIA Uses Sandboxing for Advanced Protection
Beyond Signatures: How Zscaler ZIA Uses Sandboxing for Advanced Protection
A Look at Zscaler ZIA's Cloud Sandbox
In today's ever-evolving threat landscape, relying solely on signature-based detection is like bringing a knife to a gunfight. While signatures are effective against known threats, they are powerless against the novel, zero-day attacks that increasingly bypass traditional security measures. This is where advanced technologies like cloud sandboxing come into play, and Zscaler Internet Access (ZIA) is a prime example of a platform that leverages this capability to provide robust, multi-layered protection.
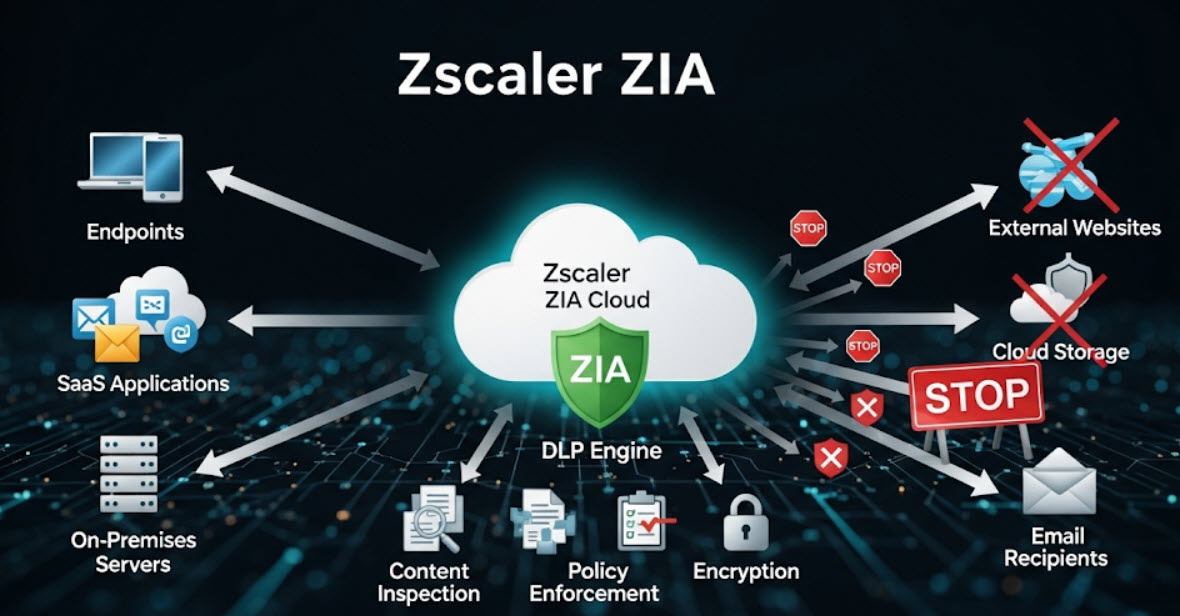
Zscaler ZIA's Cloud Sandbox is a critical component of its comprehensive security stack, designed to analyze unknown and potentially malicious files and URLs in a secure, isolated environment. This proactive approach allows ZIA to identify and neutralize threats before they can even reach your network or endpoints, significantly reducing your organization's risk exposure.
What is Cloud Sandboxing and Why is it Essential?
At its core, sandboxing involves executing suspicious files or visiting suspicious URLs within a virtualized, isolated environment that mimics a real user's system. This allows the security platform to observe the behavior of the file or website without risking infection to the actual network. If the file exhibits malicious activities—such as attempting to modify system files, communicate with command-and-control servers, or encrypt data—the sandbox can identify these behaviors and classify the file as malicious.
The necessity of sandboxing stems from several key factors:
- Evolving Threat Landscape: Cybercriminals constantly develop new evasion techniques and polymorphic malware that easily bypass traditional signature-based detection.
- Zero-Day Attacks: These are attacks that exploit vulnerabilities unknown to software vendors, meaning no signatures exist to detect them. Sandboxing is crucial for identifying these novel threats.
- Targeted Attacks: Advanced Persistent Threats (APTs) often use highly customized malware designed to evade detection. Sandboxing provides an additional layer of scrutiny.
- Increased Use of Obfuscation: Malicious actors frequently use obfuscation techniques to hide their code and intent, making static analysis difficult. Dynamic analysis in a sandbox can reveal the true nature of these files.
Zscaler's Sandbox Analysis Flow
1. User Request
Downloads unknown file
2. ZIA Inspection
Signatures & Heuristics
3. Cloud Sandbox
Detonates file in VM
4. Verdict & Action
Block or Allow access
How Zscaler ZIA's Cloud Sandbox Works
Zscaler ZIA integrates cloud sandboxing directly into its Security Service Edge (SSE) platform. When a user attempts to download a file or access a website, ZIA performs a series of checks. If a file is unknown or deemed suspicious based on initial heuristics, it is automatically forwarded to the cloud sandbox for deeper analysis.
The process is seamless for the end-user. The file is held by the Zscaler cloud while the analysis takes place. This "patient zero" protection ensures that a malicious file is never delivered. Once the analysis is complete, Zscaler's cloud-effect takes over: the hash of the malicious file is added to its global threat intelligence database, and all other Zscaler users worldwide are instantly protected from that same threat without requiring another sandbox analysis.
Inside the Sandbox: Detecting Malicious Behavior
Once a file is inside the sandbox, it undergoes intense scrutiny. The analysis goes far beyond simply running the program; ZIA's sandbox meticulously monitors for a wide range of malicious indicators of compromise (IOCs). This behavioral analysis is key to unmasking sophisticated threats that are designed to lay dormant or hide their true intentions.
Common Behaviors Analyzed
C2 Callbacks
Contacts malicious servers
Ransomware Activity
Encrypts files on disk
Registry Changes
Modifies critical settings
Privilege Escalation
Tries to gain admin rights
Dropper Activity
Downloads other malware
Evasion Techniques
Detects sandbox presence
The Final Verdict: A Proactive Defense
By integrating a powerful cloud sandbox, Zscaler ZIA shifts web filtering policy enforcement from a reactive, signature-based model to a proactive, behavior-based defense. This allows organizations to confidently defend against the most sophisticated threats, including ransomware and zero-day exploits, without compromising on performance. In the modern security landscape, this ability to analyze the unknown is no longer a luxury—it's an absolute necessity.